Security and Compliance in Digital Asset Management: Navigating the Complex Landscape
Securing digital assets within enterprises is no small feat, given the fact that 33% of digital folders in companies lack proper protection.
Plus, a whopping 96% of workstations are inadequately backed up, creating a potential minefield for data integrity.
A major player in this challenge?
Human error, consistently ranking as one of the top three causes of data loss in companies. A deep dive into how companies manage their digital assets shows a big weakness that is hard to ignore.
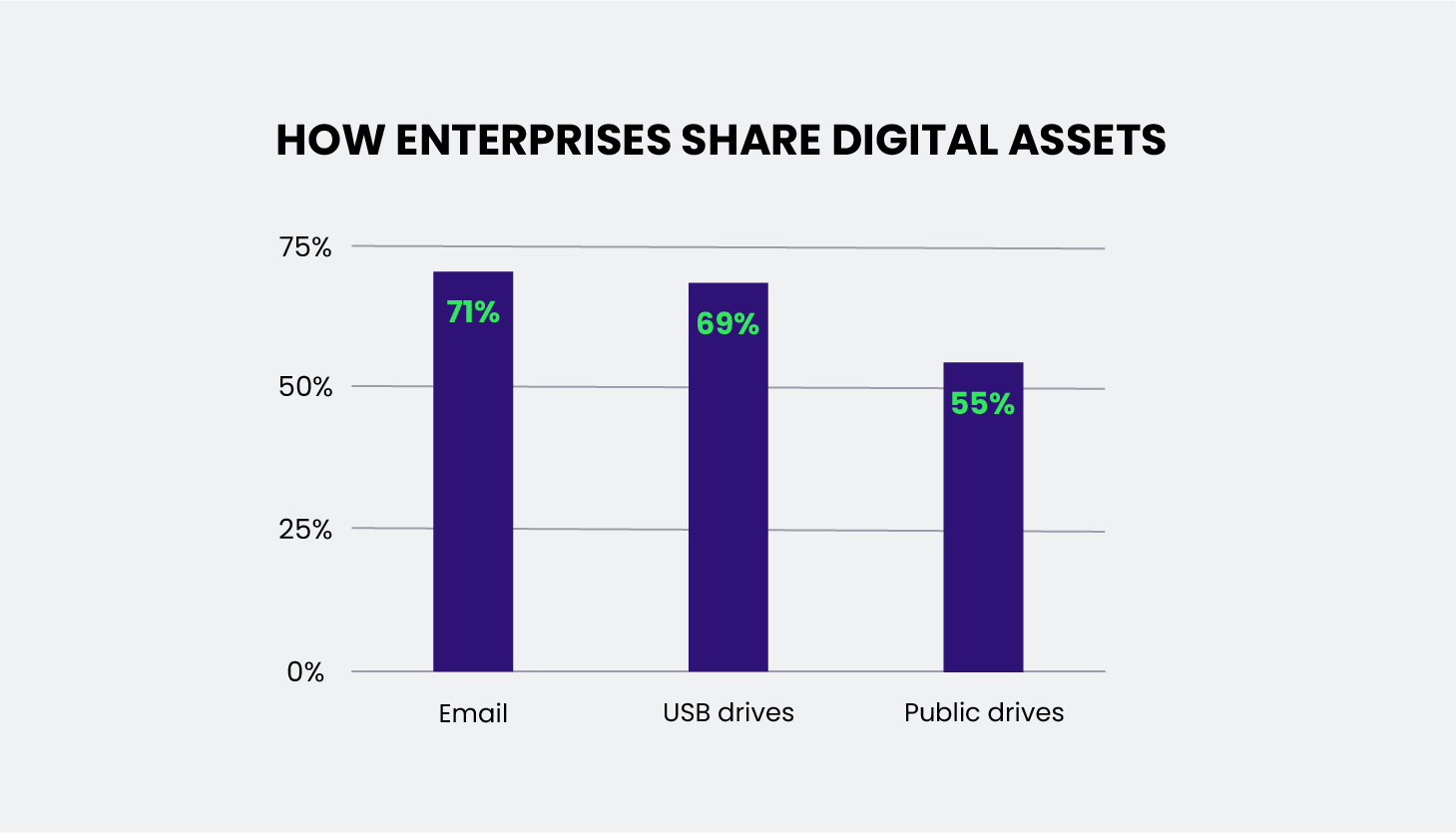
Here’s the thing: Employees usually share digital assets through familiar channels like USB drives (69%), email (71%), and public drives (55%).
Which leads to a startling 90% of companies that have experienced the loss of confidential digital assets.
So how can companies ensure an extra layer of security for their most prized digital assets, keeping them within the secure confines of their organization?
This is where Digital Asset Management (DAM) systems come in.
It's not just about preventing mistakes. It's about maintaining strategic control over sensitive organizational data, and we're here to explore just how easily DAM does this.
Table of contents:
Why enterprises need stronger content security
5 ways DAM upholds strong security and compliance
Beyond security: Optimizing DAM for enhanced performance
Conclusion
Why enterprises need stronger content security
1. To protect against data breaches
Enterprises hold a treasure trove of sensitive data, from customer details to proprietary information. Robust content security serves as a “digital fortress”, protecting against the dangers of data leaks.
2. Navigating compliance challenges
Multiple industries (like the life sciences for example) face a labyrinth of regulations governing data protection and privacy. Strengthening content security ensures a smooth journey through this regulatory maze, steering clear of any fines and legal entanglements.
3. Strengthening protection against intellectual property theft
In the competitive landscape, most enterprises have a lot of invaluable intellectual property — the lifeblood of innovation. Content security is crucial in order to avoid any attempts at IP theft or unauthorized access.
4. Tackling insider threats head-on
Threats often lurk within an organization, whether accidental (aka human error) or intentional. Having strong content security is like having a watchful ally, incorporating user behavior monitoring and access controls to stop potential breaches from within.
5. Ensuring uninterrupted business flow
Regular backups and plans for emergencies help keep content operations going smoothly, even during tough times. This keeps the company strong, allows it to continue serving customers, and reduces any kind of stoppage in work.
5 ways DAM upholds strong security and compliance
From stringent access controls to user permissions, here’s 5 ways DAM systems uphold strong security and compliance:
Access controls and user permissions
DAM systems are crucial for enterprise companies in maintaining high levels of security and compliance. Particularly through their access control and user permissions features.
These systems enable businesses to:
Implement role-based access controls: This ensures that only authorized individuals can access, modify, or delete digital assets. By assigning roles, enterprises can control who sees what, enhancing security.
Protect sensitive information: By restricting access, DAMs help safeguard confidential data and intellectual property, reducing the risk of data breaches. This is particularly relevant for industries like manufacturing, that deal with tons of sensitive information.
Ensure better compliance: Adhering to industry regulations becomes easier as DAMs can be configured to comply with legal standards, protecting against compliance risks.
Facilitate secure internal and external collaboration: Secure sharing of assets with internal teams and external partners while maintaining control over who has access to what.
Audit and reporting capabilities: They provide a trail of who accessed or modified assets, crucial for security audits and compliance reporting.
GDPR compliance
Navigating GDPR compliance is critical, and a robust DAM system proves indispensable.
What is GDPR? Short for General Data Protection Regulation, is a set of rules designed to protect the personal information of individuals in the European Union and European Economic Area, ensuring their privacy and data security.
With GDPR in effect since May 25th, 2018, businesses need to prioritize customer data protection.
A DAM system like Digizuite plays a key role by fostering transparency in data practices.
It facilitates the right to be informed through privacy notices and quick data overviews. Users gain the right of access, empowering them to confirm and access personal data.
The right to rectification is supported through interface corrections, while the right to be forgotten is managed by anonymizing data.
A comprehensive DAM system safeguards against privacy breaches and ensures compliance with GDPR parameters.
Version control
Version control in DAM systems is a game-changer for enterprises looking to boost their security and compliance.
It's like having a detailed diary for each digital asset, noting every tweak, who made it, and when.
This isn't just handy for keeping tabs on changes; it's essential for meeting those tough compliance requirements.
But there's more – version control is a safety net against data mishaps.
Accidentally deleted something important? No need to worry. With DAM, you can easily and quickly roll back to a previous version without having to dig through tons of stuffed folders with everything you don’t need inside them.
It also ensures that everyone's working with the most up-to-date, regulation-friendly versions of your assets.
Plus, it's a great way to keep everyone honest, boost collaboration, plus: Discouraging any hasty or harmful edits.
Authentication
Authentication features in DAM systems are crucial for enhancing security and compliance, particularly when external users need access to assets.
Secure methods like password-protected links and Single Sign-On (SSO) are used, with SSO allowing users to log in securely without sharing credentials across systems.
This setup is key in preventing unauthorized access and protecting sensitive information.
Modern DAMs also incorporate two-factor authentication (2FA), adding an extra security layer beyond just passwords.
This feature significantly reduces the risk of breaches, as accessing assets requires not only a password but also a second form of verification.
Lastly, DAMs enable customizable user authentication based on roles, locations, and departments.
This kind of tailored access control ensures that only authorized individuals can access specific assets, aka, further tightening security measures.
Audit log
In the DAM world, the audit log feature is a key player in upping the game of security and compliance. Consider it your meticulous record keeper, tracking every move made with your digital assets.
This is incredibly handy for quickly spotting and fixing any slip-ups. If an error does sneak in, the audit log is your ally, helping you trace it back and undo the changes with ease.
But the audit log isn’t just about mending mistakes.
It’s a vital tool for enhancing security, keeping a vigilant eye on all asset interactions. This way, any unusual or unauthorized activity gets flagged early on.
For compliance, the audit log is a lifesaver. It provides a clear, detailed history of all asset changes, aligning perfectly with regulatory requirements and making audits smoother.
Lastly: DAM systems also come with smart workflow features. These workflows add an extra safety net, requiring team reviews and approvals for key actions, thereby reducing risks like accidental overwrites.
Before any asset goes out to external collaborators, it’s thoroughly vetted, ensuring everything is top-notch and compliant.
Beyond security: Optimizing DAM for enhanced performance
Improving the use of your DAM software is not just about security. It's also about boosting performance with different extra features:
Metadata management: DAM systems excel at managing metadata, crucial for efficiently searching and categorizing digital assets. They allow you to automatically or manually generate and assign metadata, reducing manual effort and streamlining the retrieval process.
Workflow automation: DAM systems simplify the approval of digital assets by automating workflows, ensuring they align with organizational policies and boost compliance. They also handle routine tasks such as file conversions and resizing, enhancing overall efficiency. Plus, DAMs support collaboration through features like annotations and comments on assets, and enable version collaboration, allowing several users to work on the same asset while tracking every change.
Integration capabilities: DAM systems boost workflow cohesiveness by smoothly integrating with creative tools like Adobe Creative Cloud. They also provide APIs for custom integrations, letting organizations tailor the DAM system to connect with various other tools and platforms, meeting specific needs.
Asset lifecycle management: DAM systems streamline asset lifecycle management by automating the archiving and deletion of assets, based on predefined criteria. They also offer insights with content analytics, which are key for shaping content strategy and optimizing resource allocation.
Globalization and localization support: DAM systems address global needs with multi-language support, serving users across different regions. They also adhere to regional data protection and privacy laws, ensuring adaptability to various legal requirements.
Conclusion
In a nutshell, DAM systems are a powerhouse for security and efficiency in handling digital assets. They keep your digital assets safe with tight access controls, GDPR compliance, smart versioning, secure authentication, and detailed audit logs.
These features not only protect your data but also help you smoothly navigate those tricky compliance rules and protect your intellectual property.
Plus, DAMs make managing digital assets a breeze with automated workflows, easy integration with other tools, and insights on asset usage. The best DAM’s are also geared for global use, supporting multiple languages and regional compliance.
Essentially, with DAM, businesses get a secure, streamlined, and adaptable solution for managing their digital treasures in today's fast-paced world.
Ready to start safely and securely managing your digital assets through Digizuite DAM?
Get in touch with us and request a demo.
Questions from buyers:
How can I make sure my images don’t infringe on any copyright laws?
What are some best practice tips when it comes to training my team to use DAM?
How can I overcome multiple sources of truth when it comes to streamlining our content workflow?
How can I calculate the ROI of investing in a DAM for my business?